ESET Mobile Security for Android instrukcja
- Typ
- instrukcja

ESET, spol. s r.o.
ESET Mobile Security — opracowanie: ESET, spol. s r.o. Więcej informacji zawiera strona internetowa www.eset.com.
Wszelkie prawa zastrzeżone. Żadna część niniejszej dokumentacji nie może być powielana, przechowywana w systemie
pobierania ani przesyłana w jakiejkolwiek formie bądź przy użyciu jakichkolwiek środków elektronicznych,
mechanicznych, przez fotokopiowanie, nagrywanie, skanowanie lub w inny sposób bez uzyskania pisemnego zezwolenia
autora. ESET, spol. s r.o. zastrzega sobie prawo do wprowadzania zmian w dowolnych elementach opisanego
oprogramowania bez uprzedniego powiadomienia.
Dział obsługi klienta: http://support.eset.com/
WER. 30. 1. 2017

Spis treści
...........................................................................................................................4
Wstęp1.
..........................................................................................................................................................................................................4Nowe funkcje w wersji 3,51.1
..........................................................................................................................................................................................................4Minimalne wymagania systemowe1.2
...........................................................................................................................5
Instalacja2.
..........................................................................................................................................................................................................5Pobieranie ze sklepu Google Play2.1
..........................................................................................................................................................................................................5Pobieranie ze strony internetowej firmy ESET2.2
..........................................................................................................................................................................................................6Kreator uruchamiania2.3
...........................................................................................................................9
Odinstalowanie3.
...........................................................................................................................9
Aktywacja produktu4.
...........................................................................................................................10
Antywirus5.
..........................................................................................................................................................................................................12Skanowania automatyczne5.1
..........................................................................................................................................................................................................13Dzienniki skanowania5.2
..........................................................................................................................................................................................................14Ustawienia zaawansowane5.3
...........................................................................................................................15
Anti-Theft6.
..........................................................................................................................................................................................................16Portal internetowy6.1
...............................................................................................................................................................................................17Optymalizacja
6.1.1
...............................................................................................................................................................................................17Ochrona proaktywna
6.1.2
..........................................................................................................................................................................................................17Ochrona SIM6.2
...............................................................................................................................................................................................18Zaufane karty SIM
6.2.1
...............................................................................................................................................................................................18Zaufani odbiorcy
6.2.2
..........................................................................................................................................................................................................19Polecenia SMS6.3
..........................................................................................................................................................................................................20Ustawienia6.4
...............................................................................................................................................................................................20Hasło zabezpieczeń
6.4.1
...............................................................................................................................................................................................20Szczegóły kontaktu
6.4.2
...........................................................................................................................21
Ochrona przed atakami typu „phishing”7.
...........................................................................................................................22
Filtr SMS-ów i połączeń8.
..........................................................................................................................................................................................................22Reguły8.1
...............................................................................................................................................................................................23Dodawanie nowej reguły
8.1.1
..........................................................................................................................................................................................................23Historia8.2
...........................................................................................................................23
Audyt zabezpieczeń9.
..........................................................................................................................................................................................................24Monitorowanie urządzenia9.1
..........................................................................................................................................................................................................25Audyt aplikacji9.2
...........................................................................................................................26
Raport zabezpieczeń10.
...........................................................................................................................27
Ustawienia11.
...........................................................................................................................28
Dział obsługi klienta12.

4
1. Wstęp
ESET Mobile Security to kompletne rozwiązanie zabezpieczające, które chroni urządzenie przed pojawiającymi się
zagrożeniami i stronami wyłudzającymi dane, filtruje niechciane połączenia i wiadomości oraz umożliwia zdalne
przejęcie kontroli nad urządzeniem w przypadku jego utraty lub kradzieży.
Główne funkcje to:
Antywirus
Anti-Theft
Ochrona przed atakami typu „phishing”
Integracja z portalem My Eset
Filtr SMS-ów i połączeń
Audyt zabezpieczeń
Raport zabezpieczeń
1.1 Nowe funkcje w wersji 3,5
Poniższe aktualizacje i usprawnienia zostały wprowadzone w programie ESET Mobile Security 3.5:
Ochrona proaktywna
Ulepszona ochrona przed atakami typu „phishing”
Raport zabezpieczeń
Uprawnienia systemu są łatwo dostępne z poziomu programu ESET Mobile Security
Ostatnia znana lokalizacja urządzenia zapisana w funkcji ESET Anti-Theft przed rozładowaniem się baterii
1.2 Minimalne wymagania systemowe
Aby można było zainstalować program ESET Mobile Security, urządzenie z systemem Android musi spełniać
następujące minimalne wymagania systemowe:
System operacyjny: Android 4 (Ice Cream Sandwich) lub nowszy
Rozdzielczość ekranu dotykowego: minimum 480x800 pikseli
Procesor: ARM z zestawem instrukcji ARMv7+, x86 Intel Atom
Pamięć RAM: 128 MB
Wolne miejsce w pamięci wewnętrznej: 20 MB
Połączenie internetowe
UWAGA: Urządzenia z dwiema kartami SIM oraz urządzenia z pełną kontrolą nad systemem nie są obsługiwane.
Funkcje Anti-Theft oraz Filtr SMS-ów i połączeń nie są dostępne na tabletach nieobsługujących połączeń i
wiadomości.

5
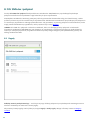
2. Instalacja
ESET Mobile Security — ta aplikacja jest dostępna do pobrania przy użyciu poniższych kanałów dystrybucji:
Sklep Google Play — ta aplikacja otrzymuje regularne aktualizacje za pośrednictwem sklepu Google
Play
Strona internetowa firmy ESET — ta aplikacja otrzymuje aktualizacje z systemu aktualizacji
sprawdzającego dostępność wersji ESET
Amazon Appstore
Aby można było chronić dane osobowe i zasoby na urządzeniu z Androidem, program ESET Mobile Security
potrzebuje dostępu do funkcji urządzenia, a w niektórych przypadkach kontroli nad tymi funkcjami. Szczegółowe
omówienie każdego typu uprawnienia oraz sposobu jego używania zawiera tabela w tym artykule bazy wiedzy:
http://support.eset.com/kb2711/#PrivacyPolicy
Ten artykuł nie jest dostępny we wszystkich językach.
2.1 Pobieranie ze sklepu Google Play
Na urządzeniu z systemem Android otwórz aplikację Google Play Store i wyszukaj nazwę ESET Mobile Security (lub
tylko ESET).
Możesz też użyć łącza lub zeskanować poniższy kod QR przy użyciu urządzenia mobilnego i aplikacji do skanowania
kodów QR:
https://play.google.com/store/apps/details?id=com.eset.ems2.gp
2.2 Pobieranie ze strony internetowej firmy ESET
Dostępność wersji na stronie internetowej różni się zależnie od regionu.
1. Pobierz plik instalacyjny APK ze strony internetowej firmy ESET.
2. Upewnij się, że na urządzeniu dozwolone są aplikacje z nieznanych źródeł . W tym celu naciśnij ikonę programu
uruchamiającego na ekranie głównym systemu Android (lub przejdź do obszaru Ekran główny > Menu).
Naciśnij kolejno opcje Ustawienia > Zabezpieczenia. Pole Nieznane źródła musi być zaznaczone.
3. Otwórz plik z obszaru powiadomień systemu Android lub odszukaj go, przeglądając pliki. Plik zostaje zwykle
zapisany w folderze Pobrane.
4. Naciśnij pozycję Instaluj , a następnie pozycję Otwórz.

6
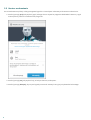
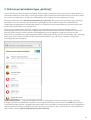
2.3 Kreator uruchamiania
Po zainstalowaniu aplikacji należy postępować zgodnie z instrukcjami ekranowymi kreatora uruchamiania:
1. Naciśnij pozycję Język, aby wybrać język, którego chcesz używać w programie ESET Mobile Security. Język
można później zmienić w ustawieniach programu.
2. Naciśnij pozycję Kraj, aby wybrać kraj, w którym obecnie przebywasz.
3. Naciśnij pozycję Akceptuj, aby wyrazić zgodę na warunki Umowy licencyjnej użytkownika końcowego.

7
4. Naciśnij pozycję Akceptuj na ekranie Zgoda użytkownika. Niektóre informacje, na przykład dotyczące
lokalizacji urządzenia i odwiedzonych stron internetowych, mogą być udostępniane firmie ESET.
5. Naciśnij pozycję Dalej , jeśli chcesz korzystać z usługi ESET Live Grid. Można to później zmienić w ustawieniach
programu. Więcej informacji zawiera ta sekcja.

8
6. Wybierz pozycję Włącz wykrywanie lub Nie włączaj wykrywania, aby określić, czy program ESET Mobile
Security będzie wykrywać potencjalnie niepożądane aplikacje, a następnie naciśnij pozycję Dalej. Można to
później zmienić w ustawieniach programu. Więcej informacji na temat potencjalnie niepożądanych aplikacji
zawiera ta sekcja.
7. W następnym kroku zostanie wyświetlona lista wszystkich kont e-mail dostępnych na urządzeniu. Wybierz
konto, którego firma ESET ma używać na potrzeby komunikacji związanej z rejestracją licencji na produkt,
informacjami o resetowaniu hasła zabezpieczeń i komunikacji z działem obsługi ESET. Jeśli lista nie zawiera
żadnego konta e-mail, naciśnij pozycję Dodaj konto > OK > Istniejące, aby zalogować się na istniejącym koncie
e-mail, lub naciśnij Nowe, aby utworzyć nowe konto.
8. Naciśnij pozycję Aktywuj, aby aktywować funkcje premium produktu, lub naciśnij pozycję Pomiń, aby
rozpocząć używanie wersji darmowej.

9
3. Odinstalowanie
ESET Mobile Security można odinstalować przy użyciu kreatora odinstalowania dostępnego w menu głównym
programu. Naciśnij kolejno pozycje Menu > Ustawienia > Odinstaluj. Zostanie wyświetlona prośba o
wprowadzenie hasła zabezpieczeń.
Można też wykonać poniższe kroki, aby ręcznie odinstalować produkt:
1. Naciśnij ikonę programu uruchamiającego na ekranie głównym systemu Android (lub przejdź do pozycji
Ekran główny > Menu) i naciśnij kolejno pozycje Ustawienia > Zabezpieczenia > Administratorzy urządzenia.
Wybierz pozycję ESET Mobile Security i naciśnij pozycję Dezaktywuj. Naciśnij pozycję Odblokuj i wpisz hasło
zabezpieczeń. Możesz pominąć ten krok, jeśli aplikacja nie jest już zdefiniowana jako administrator
urządzenia.
2. Wróć do obszaru Ustawienia i naciśnij kolejno pozycje Zarządzaj aplikacjami > ESET Mobile Security >
Odinstaluj.
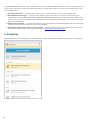
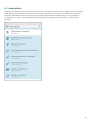
4. Aktywacja produktu
ESET Mobile Security ma trzy dostępne wersje:
Wersja darmowa — z podstawowych funkcji można korzystać za darmo przez nieograniczony czas
Wersja próbna — funkcje premium są aktywne przez ograniczony czas (domyślnie przez 30 dni)
Premium — funkcje premium są aktywne do chwili wygaśnięcia licencji
Poniższa tabela zawiera informacje o funkcjach dostępnych w wersji darmowej, próbnej oraz w wersji Premium:
Wersja darmowa
Wersja próbna i Premium
Antywirus
Antywirus — skanowania
automatyczne
Automatyczne aktualizacje bazy
danych wirusów
Anti-Theft — polecenia SMS (oprócz
polecenia Wyczyść)
Anti-Theft — portal internetowy
Anti-Theft — ochrona SIM
Ochrona przed atakami typu
„phishing”
Filtr SMS-ów i połączeń
Audyt zabezpieczeń
Raport zabezpieczeń
Aby aktywować program ESET Mobile Security bezpośrednio na urządzeniu z systemem Android, naciśnij pozycję
Menu na ekranie głównym programu ESET Mobile Security (lub naciśnij przycisk MENU na urządzeniu) i naciśnij
pozycję Licencja.

10
Program ESET Mobile Security można aktywować na kilka sposobów. Dostępność danej metody aktywacji może się
różnić zależnie od kraju, a także od sposobu dystrybucji (strona internetowa firmy ESET, sklep Google Play, sklep
Amazon Appstore).
Kup wersję Premium — tę opcję należy wybrać, jeśli nie masz licencji i chcesz ją kupić Google Play.
Wprowadź klucz licencyjny — tę opcję należy wybrać, jeśli już masz klucz licencyjny. Klucz licencyjny to
niepowtarzalny ciąg znaków w formacie: XXXX-XXXX-XXXX-XXXX-XXXX Służy on do identyfikacji właściciela
licencji. Klucz licencyjny znajduje się w wiadomości e-mail otrzymanej od firmy ESET lub na karcie licencyjnej
dołączonej do pudełka.
Aktywuj wersję próbną — tę opcję należy wybrać, aby wypróbować program ESET Mobile Security przed jego
kupnem. Jest to możliwe tylko przy użyciu konta Google.
Mam nazwę użytkownika i hasło. Co należy zrobić? — tę opcję należy wybrać, aby przekonwertować nazwę
użytkownika i hasło na klucz licencyjny pod adresem https://my.eset.com/convert
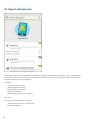
5. Antywirus
Moduł Antywirus chroni urządzenie przed szkodliwym kodem, blokując pojawiające się zagrożenia i usuwając je.

11
Skanowanie urządzenia
Określone wstępnie zdefiniowane typy plików są skanowane domyślnie. Skanowanie urządzenia polega na
sprawdzeniu pamięci, uruchomionych procesów, bibliotek dołączanych dynamicznie zależnych od tych procesów
oraz plików w pamięci wewnętrznej i zewnętrznej wymiennej pamięci masowej. Krótkie podsumowanie wyników
skanowania jest zapisywane w dzienniku dostępnym w sekcji Dzienniki skanowania. Aby przerwać trwające
skanowanie, należy nacisnąć ikonę .
Poziom skanowania
Istnieją 2 poziomy skanowania:
Inteligentne — umożliwia skanowanie zainstalowanych aplikacji, plików DEX (plików wykonywalnych systemu
operacyjnego Android), plików SO (bibliotek) oraz archiwów przy maksymalnej głębokości skanowania
sięgającej 3 archiwów zagnieżdżonych, a także zawartości kart SD.
Dokładne — obejmuje wszystkie typy plików, zarówno w pamięci wewnętrznej, jak i na karcie SD, bez względu
na ich rozszerzenie.
Aktualizuj bazę sygnatur wirusów
Domyślnie program ESET Mobile Security jest instalowany wraz ze zdefiniowanym zadaniem aktualizacji, które
zapewnia regularne aktualizowanie programu. Aby ręcznie uruchomić aktualizację, należy nacisnąć pozycję
Aktualizuj bazę sygnatur wirusów.
UWAGA: Aby zapobiec niepotrzebnemu wykorzystywaniu przepustowości, aktualizacje są publikowane w razie
potrzeby, czyli gdy zostanie dodane nowe zagrożenie. Aktualizacje są udostępniane bezpłatnie, operator sieci może
jednak pobierać opłaty za transfer danych.
Więcej informacji na temat skanowania można uzyskać po kliknięciu poniższych linków:
Skanowania automatyczne
Dzienniki skanowania
Ustawienia zaawansowane

12
5.1 Skanowania automatyczne
Oprócz skanowania urządzenia na żądanie w programie ESET Mobile Security dostępne są również opcje skanowania
automatycznego.
Poziom skanowania
Istnieją 2 poziomy skanowania. To ustawienie dotyczy zarówno opcji Skanowanie podczas ładowania, jak i opcji
Planowane skanowanie:
Inteligentne — umożliwia skanowanie zainstalowanych aplikacji, plików DEX (plików wykonywalnych systemu
operacyjnego Android), plików SO (bibliotek) oraz archiwów przy maksymalnej głębokości skanowania
sięgającej 3 archiwów zagnieżdżonych, a także zawartości kart SD.
Dokładne — obejmuje wszystkie typy plików, zarówno w pamięci wewnętrznej, jak i na karcie SD, bez względu
na ich rozszerzenie.
Skanowanie podczas ładowania
Po wybraniu tej opcji skanowanie jest uruchamiane automatycznie, gdy urządzenie jest w stanie bezczynności (a
ponadto jest w pełni naładowane i podłączone do ładowarki).

13
Planowane skanowanie
Planowane skanowanie umożliwia zaplanowanie skanowania urządzenia, aby było uruchamiane w ustalonym
czasie. Aby zaplanować skanowanie, naciśnij przełącznik obok opcji Planowane skanowanie i określ daty oraz
godziny uruchomienia skanowania.
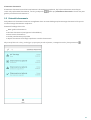
5.2 Dzienniki skanowania
Sekcja Dzienniki skanowania zawiera szczegółowe dane na temat każdego zaplanowanego skanowania lub ręcznie
uruchomionego skanowania urządzenia.
Zawartość każdego dziennika:
Data i godzina skanowania
Poziom skanowania (Inteligentne lub Dokładne)
Czas trwania skanowania
Liczba przeskanowanych plików
Wyniki skanowania lub błędy napotkane w trakcie skanowania
Aby usunąć dziennik z listy, naciśnij go i przytrzymaj w celu wybrania, a następnie naciśnij ikonę usuwania .

14
5.3 Ustawienia zaawansowane
Ochrona w czasie rzeczywistym
Skaner działający w czasie rzeczywistym uruchamia się automatycznie wraz z systemem i skanuje znajdujące się w
nim pliki. Automatycznie skanuje folder Download oraz zainstalowane lub zaktualizowane aplikacje.
ESET Live Grid
ESET Live Grid to zaawansowana technologia wczesnego ostrzegania oparta na rozwiązaniu ThreatSense.Net, której
celem jest zapewnienie dodatkowej ochrony urządzenia. Stale monitoruje ona programy i procesy uruchamiane
przez system, wykorzystując dane zebrane od milionów użytkowników produktów ESET na całym świecie. Ponadto
skanowanie odbywa się z coraz większą szybkością i precyzją w miarę rozrastania się bazy danych technologii ESET
Live Grid. Umożliwia to oferowanie skuteczniejszej ochrony proaktywnej i zwiększonej prędkości skanowania
wszystkim użytkownikom oprogramowania ESET. Zalecamy włączenie tej funkcji. Dziękujemy za pomoc.

15
Wykryj potencjalnie niepożądane aplikacje
Potencjalnie niepożądana aplikacja jest programem zawierającym oprogramowanie typu adware powodującym
instalowanie pasków narzędzi, śledzącym wyniki wyszukiwania lub mającym niejasne działanie. W niektórych
sytuacjach może okazać się, że korzyści oferowane przez potencjalnie niepożądaną aplikację przeważają ryzyko. Z
tego powodu firma ESET przydziela takim aplikacjom kategorię niskiego ryzyka w porównaniu z innymi typami
szkodliwego oprogramowania.
Wykryj potencjalnie niebezpieczne aplikacje
Istnieje wiele uznanych aplikacji, których zadaniem jest ułatwianie zarządzania urządzeniami pracującymi w sieci.
Jednak w nieodpowiednich rękach te aplikacje mogą być wykorzystywane do nieuprawnionych działań. Włączenie
opcji Wykryj potencjalnie niebezpieczne aplikacje umożliwia monitorowanie tego typu aplikacji i blokowanie ich
zgodnie z uznaniem użytkownika. Potencjalnie niebezpieczne aplikacje to kategoria, do której należą niektóre
legalne programy komercyjne. Obejmuje ona takie programy, jak narzędzia do zdalnego dostępu, aplikacje do
łamania haseł i programy rejestrujące znaki wprowadzane na klawiaturze.
Aktualizacje bazy sygnatur wirusów
Ta opcja umożliwia ustawienie przedziału czasowego pomiędzy kolejnymi automatycznymi pobraniami bazy danych
zagrożeń. Aktualizacje są publikowane w razie potrzeby, gdy do bazy danych zostanie dodane nowe zagrożenie.
Zalecamy pozostawienie domyślnego ustawienia tej opcji (codziennie).
Serwer aktualizacji
Ta opcja umożliwia włączenie aktualizacji urządzenia z serwera wersji wstępnej. Aktualizacje w wersji wstępnej
przeszły wszechstronne testy wewnętrzne i wkrótce zostaną udostępnione do ogólnego użytku. Ich włączenie
przynosi korzyść w postaci dostępu do najnowszych metod wykrywania i poprawek. Aktualizacje te mogą być jednak
czasami niestabilne. Aby sprawdzić wersje bieżących modułów programu, naciśnij pozycję menu na ekranie
głównym programu ESET Mobile Security, a następnie naciśnij kolejno pozycje Informacje > ESET Mobile Security. W
przypadku zwykłych użytkowników zalecane jest pozostawienie domyślnie wybranej opcji Serwer wersji.
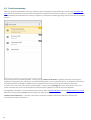
6. Anti-Theft
Funkcja Anti-Theft chroni urządzenie mobilne przed nieupoważnionym dostępem.
Jeśli telefon zostanie zgubiony lub skradziony i ktoś wymieni w nim kartę SIM na nową (niezaufaną), telefon
zostanie automatycznie zablokowany przez program ESET Mobile Security, a na zdefiniowane przez użytkownika
numery telefonów zostanie wysłana wiadomość SMS. Wiadomość ta będzie zawierała numer telefonu obecnie
włożonej karty SIM, numer IMSI (International Mobile Subscriber Identity — międzynarodowy identyfikator
abonenta) oraz numer IMEI (International Mobile Equipment Identity — międzynarodowy identyfikator urządzenia)
telefonu. Nieautoryzowany użytkownik nie będzie wiedział, że ta wiadomość została wysłana, gdyż zostanie ona
automatycznie usunięta z wątków w aplikacji Wiadomości. Można też pobrać współrzędne GPS zgubionego
urządzenia lub zdalnie usunąć wszystkie dane zapisane na urządzeniu.
UWAGA: Niektóre możliwości funkcji Anti-Theft (Zaufane karty SIM i Polecenia SMS) nie są dostępne na
urządzeniach nieobsługujących wiadomości.

16
6.1 Portal internetowy
Wersja 3 programu ESET Mobile Security zapewnia pełną integrację z ochroną ESET Anti-Theft dzięki portalowi My
Eset. Portal ten umożliwia monitorowanie aktywności urządzenia, blokowanie urządzenia, wysyłanie
niestandardowych wiadomości do znalazcy urządzenia, uruchamianie bardzo głośnego alarmu oraz zdalne usuwanie
danych.
Aby utworzyć konto w portalu My ESET, naciśnij pozycję Utwórz nowe konto i wypełnij formularz rejestracyjny.
Sprawdź w swojej skrzynce odbiorczej, czy nadeszła wiadomość e-mail z potwierdzeniem, a następnie kliknij łącze,
by aktywować konto. Następnie będzie można zarządzać funkcjami Anti-Theft za pomocą konta w portalu
my.eset.com. Jeśli masz już konto w portalu My ESET, naciśnij pozycję Zaloguj się i wpisz swój adres e-mail oraz
hasło. Po wykonaniu tych czynności będzie można powiązać urządzenie z kontem w portalu My ESET.
Szczegółowe informacje na temat używania funkcji Anti-Theft w portalu My ESET zawiera pomoc online Anti-Theft.
Można też kliknąć pozycję Pomoc w prawym górnym rogu ekranu.
Ostatnia znana lokalizacja — zapisuje informacje o lokalizacji urządzenia w funkcji ESET Anti-Theft przed
wyczerpaniem baterii urządzenia.

17
6.1.1 Optymalizacja
Optymalizacja przeprowadzana przez funkcję ESET Anti-Theft polega na wymiernej ocenie technicznej stanu
bezpieczeństwa urządzenia. Ochrona Anti-Theft sprawdza system pod kątem wymienionych poniżej problemów.
W przypadku każdego problemu z zabezpieczeniami można nacisnąć pozycję Zmień ustawienia, aby przejść na ekran
umożliwiający rozwiązanie tego problemu. Aby produkt ESET Mobile Security nie zgłaszał danego zagrożenia jako
problemu, należy nacisnąć opcję Ignoruj to zagrożenie.
Wyłączone usługi lokalizacji — aby je włączyć, należy wybrać kolejno pozycje Ustawienia systemu Android >
Usługi lokalizacji i wybrać pozycję Używaj sieci bezprzewodowych.
Niekorzystanie z satelitów GPS — dostęp do odpowiedniego ustawienia jest możliwy po wybraniu kolejno
pozycji Ustawienia systemu Android > Lokalizacja > Tryb > Wysoka dokładność.
Niezabezpieczona blokada ekranu — aby zabezpieczyć urządzenie przy użyciu kodu ekranu blokady, hasła,
kodu PIN lub wzoru, należy wybrać kolejno pozycje Ustawienia systemu Android > Zabezpieczenie ekranu >
Blokada ekranu i wybrać jedną z dostępnych opcji. W większości urządzeń z systemem Android odblokowanie
następuje po przesunięciu palcem po ekranie, wykonaniu ruchu, rozpoznaniu twarzy, rozpoznaniu twarzy i
głosu, narysowania wzoru, podaniu kodu PIN lub hasła. Gdy ktoś próbuje odblokować urządzenie z użyciem
nieprawidłowego kodu, funkcja ESET Anti-Theft wysyła do użytkownika powiadomienie o podejrzanym
działaniu za pośrednictwem portalu My Eset.
Niewłączona obsługa danych mobilnych — dostęp do odpowiedniego ustawienia jest możliwy po wybraniu
kolejno pozycji Ustawienia systemu Android > Połączenia bezprzewodowe i sieci > Sieci komórkowe > Dane.
Brak usług Google Play — funkcja ESET Anti-Theft używa usług Google Play do dostarczania poleceń na
urządzenie w czasie rzeczywistym i wyświetlania poleceń wypychanych. Jeśli te usługi są wyłączone lub
brakuje ich na urządzeniu, zakres funkcji ESET Anti-Theft, którymi można zarządzać w portalu My Eset, jest
ograniczony. W takiej sytuacji zalecamy korzystanie z poleceń SMS, zamiast z portalu My Eset.
6.1.2 Ochrona proaktywna
Ta funkcja umożliwia dostosowywanie ostrzeżeń i działań wyzwalanych w trybie Podejrzane, w którym program
ESET Mobile Security regularnie zapisuje lokalizację urządzenia, zdjęcia z aparatu i adresy IP w sieci Wi-Fi. Można
skonfigurować następujące opcje:
Aktywuj po nieudanym odblokowaniu — ta opcja jest domyślnie włączona. Blokuje urządzenie po wpisaniu
nieprawidłowego kodu blokady ekranu
Maksymalna liczba niepowodzeń odblokowania — dozwolona liczba odblokowań zakończonych
niepowodzeniem
Czas na poprawienie — domyślny czas na wpisanie prawidłowego kodu odblokowania wynosi 15 sekund
Zapisz zdjęcia na urządzeniu — zapisuje zdjęcia wykonane przy użyciu tylnego i przedniego aparatu w galerii
urządzenia oraz w portalu Anti-Theft w wypadku niepowodzenia odblokowania lub wyjęcia karty SIM
6.2 Ochrona SIM
Aby rozpocząć używanie funkcji Ochrona SMS, w menu głównym programu naciśnij kolejno pozycje Anti-Theft >
Ochrona SIM i naciśnij przełącznik w celu włączenia tej funkcji. Prosty kreator poprowadzi Cię przez proces
konfiguracji. Czynności te możesz też wykonać przy użyciu kreatora konfiguracji poleceń SMS:
Wpisz hasło zabezpieczeń
Dodaj szczegóły kontaktu
Włącz ochronę przed odinstalowaniem
Zapisz bieżącą kartę SIM jako zaufaną
Dodaj zaufanego odbiorcę

18
6.2.1 Zaufane karty SIM
W sekcji Zaufane karty SIM dostępna jest lista zaufanych kart SIM akceptowanych przez program ESET Mobile
Security. Po włożeniu karty SIM niewymienionej na tej liście nastąpi zablokowanie ekranu i wysłanie wiadomości
SMS z alertem do zaufanych odbiorców.
Aby dodać nową kartę SIM, naciśnij ikonę . Wpisz nazwę w polu NAZWA KARTY SIM (np. Dom, Praca) oraz jej
numer IMSI (International Mobile Subscriber Identity, międzynarodowy identyfikator abonenta). Numer IMSI jest
zazwyczaj prezentowany w postaci 15-cyfrowego numeru wydrukowanego na karcie SIM. W niektórych przypadkach
ten numer może być krótszy.
Aby usunąć kartę SIM z listy, wybierz ją i naciśnij ikonę .
UWAGA: funkcja Zaufane karty SIM nie jest dostępna na urządzeniach obsługujących tylko technologię CDMA,
WCDMA lub Wi-Fi.
6.2.2 Zaufani odbiorcy
W sekcji Zaufani odbiorcy można dodawać lub usuwać numery telefonów znajomych i członków rodziny. Osoby,
których numer został dodany, mogą:
otrzymywać SMS-y z alertem po wykryciu nieautoryzowanej karty SIM w urządzeniu,
resetować hasło zabezpieczeń (jeśli dla kontaktu włączona jest opcja Zezwól na zdalne zresetowanie hasła
zabezpieczeń).
W celu dodania nowego zaufanego odbiorcę naciśnij ikonę i wpisz jego nazwę i numer telefonu komórkowego
lub naciśnij ikonę , aby wybrać kontakt z listy kontaktów telefonu. Aby usunąć zaufanego odbiorcę, wybierz jego
pozycję i naciśnij ikonę usuwania .
Jeśli pozycja zaufanego odbiorcy zawiera więcej niż jeden numer telefonu, wysłanie SMS-a z alertem i zresetowanie
hasła będzie możliwe w przypadku wszystkich powiązanych z tą pozycją numerów.
UWAGA: w przypadku pobytu za granicą wszystkie numery telefonów na liście muszą być poprzedzone
międzynarodowym numerem kierunkowym (np. +1610100100).

19
6.3 Polecenia SMS
Aby rozpocząć używanie poleceń SMS, w menu głównym programu naciśnij kolejno pozycje Anti-Theft > Polecenia
SMS i naciśnij przełącznik w celu włączenia tej funkcji. Jeśli wykonano już czynności w kreatorze Ochrona SIM,
podczas tej konfiguracji zostanie wyświetlona tylko prośba o wpisanie jednego dodatkowego parametru — hasła
SMS. Jako hasło SMS można wpisać hasło zabezpieczeń. Nie jest to jednak zalecane, ponieważ hasło SMS będzie
widoczne na ekranie urządzenia mobilnego w wiadomościach przychodzących.
Można wysyłać następujące polecenia SMS:
Odblokuj
eset remote reset
Wysłanie tego polecenia z urządzenia zaufanego odbiorcy powoduje odblokowanie ekranu urządzenia.
Zablokuj
eset lock hasło
To polecenie blokuje urządzenie, które będzie można odblokować przy użyciu hasła zabezpieczeń.
Alarm
eset siren hasło
Uruchamia głośny alarm, nawet jeśli urządzenie jest wyciszone.
Znajdź
eset find hasło
Użytkownik otrzymuje wiadomość tekstową ze współrzędnymi GPS urządzenia docelowego oraz łączem do jego
lokalizacji w Mapach Google. W przypadku uzyskania bardziej precyzyjnych danych lokalizacji urządzenie ponownie
wysyła wiadomość SMS.

20
Wyczyść
eset wipe hasło
Wszystkie kontakty, wiadomości, wiadomości e-mail, konta, zawartość karty SD, zdjęcia, muzyka i filmy zapisane w
domyślnych folderach zostają trwale usunięte z urządzenia. ESET Mobile Security pozostaje zainstalowany.
UWAGA: chociaż w poleceniach SMS nie jest rozróżniana wielkość liter, musi zostać wpisane dokładnie takie hasło,
jakie zostało zdefiniowane w kreatorze konfiguracji funkcji Anti-Theft.
6.4 Ustawienia
W sekcji Ustawienia funkcji Anti-Theft dostępne są te elementy:
Hasło zabezpieczeń
Szczegóły kontaktu
6.4.1 Hasło zabezpieczeń
Hasło zabezpieczeń jest wymagane do odblokowania urządzenia, dostępu do funkcji Anti-Theft, odinstalowania
programu ESET Mobile Security i wysyłania poleceń SMS (jeśli ta opcja została włączona podczas tworzenia hasła
SMS).
Czynności, które można wykonać w przypadku zapomnienia hasła zabezpieczeń:
Wyślij na swój numer wiadomość tekstową z numeru telefonu zaufanego odbiorcy. Wiadomość musi mieć
następującą postać: eset remote reset
Jeśli urządzenie jest połączone z Internetem, poproś o kod resetowania hasła, naciskając pozycję Wiadomości
e-mail na zablokowanym urządzeniu. Wiadomość e-mail zawierająca kod weryfikacyjny zostanie wysłana na
konto e-mail Google zdefiniowane podczas instalacji. Wpisz kod weryfikacyjny oraz nowe hasło na
zablokowanym ekranie.
Zresetuj hasło w portalu My Eset. Po zalogowaniu się wybierz urządzenie, kliknij pozycję Ustawienia i wpisz
nowe hasło.
Jeśli urządzenie nie jest połączone z Internetem, wypełnij formularz wskazany w tym artykule bazy wiedzy.
Skontaktuj się z Działem obsługi klienta firmy ESET, jeśli nie możesz wysłać wspomnianych wcześniej danych.
WAŻNE: aby utworzyć bezpieczne hasło, które trudniej jest odgadnąć, użyj połączenia małych liter, dużych liter i
cyfr.
6.4.2 Szczegóły kontaktu
Jeśli urządzenie zostanie oznaczone jako zgubione w portalu my.eset.com, informacje z sekcji Szczegóły kontaktu
zostaną wyświetlone na ekranie zablokowanego urządzenia, aby pomóc jego znalazcy skontaktować się z Tobą.
Te informacje mogą obejmować te elementy:
Nazwa (opcjonalnie)
Zapasowy numer telefonu członka rodziny lub znajomego
Opis urządzenia (opcjonalnie)
Adres e-mail (opcjonalnie)
Strona się ładuje...
Strona się ładuje...
Strona się ładuje...
Strona się ładuje...
Strona się ładuje...
Strona się ładuje...
Strona się ładuje...
Strona się ładuje...
-
 1
1
-
 2
2
-
 3
3
-
 4
4
-
 5
5
-
 6
6
-
 7
7
-
 8
8
-
 9
9
-
 10
10
-
 11
11
-
 12
12
-
 13
13
-
 14
14
-
 15
15
-
 16
16
-
 17
17
-
 18
18
-
 19
19
-
 20
20
-
 21
21
-
 22
22
-
 23
23
-
 24
24
-
 25
25
-
 26
26
-
 27
27
-
 28
28
ESET Mobile Security for Android instrukcja
- Typ
- instrukcja
Powiązane artykuły
-
ESET Endpoint Security for Android instrukcja
-
ESET Mobile Security for Android 9 Google Play Instrukcja obsługi
-
ESET Smart TV Security 2 Instrukcja obsługi
-
ESET Internet Security 14 Instrukcja obsługi
-
ESET Smart Security Premium 14 Instrukcja obsługi
-
ESET myESET Instrukcja obsługi
-
ESET Smart Security Premium 12 Instrukcja obsługi
-
ESET Smart Security Premium instrukcja
-
ESET Internet Security 12 Instrukcja obsługi
-
ESET Internet Security 13 Instrukcja obsługi




























